Concepts
In this article, we will introduce some “familiar” types of viruses that affect home users. Some of these types are virtually “extinct” because they haven’t kept pace with the advancements in computers and the Internet, primarily spreading within infected subjects, posing low risks, and being easily detected. However, this is not good news, as we must continue to “face off” against the next generation of viruses: they are more cunning, malicious, spread faster, and have devastating destructive capabilities…
Virus: A virus is a piece of code, a small program designed to perform certain actions on an infected computer without permission or knowledge of the user. They have the ability to self-replicate, spreading to other files and programs on the computer and to other computers. Computer viruses are usually classified into several types, including: File viruses (Jerusalem, Cascade…) that infect files of commonly used software in the Windows operating system, such as .com, .exe, .bat, .pif, .sys files; Boot viruses (Disk Killer, Michelangelo, Stoned…) that infect the code in the boot sector of the hard drive; Macro viruses (W97M.Melissa, WM.NiceDay, W97M.Groov…) that infect files in MS Office. Additionally, there are other types of viruses like hybrid viruses (a combination of boot viruses and file viruses), master boot record viruses…
Trojan Horse: These are programs disguised as harmless but contain dangerous code aimed at stealing personal information, opening ports for hackers to infiltrate, turning the infected computer into a source of spam dissemination, or becoming a tool to attack a specific website, such as W32.Mimic. Unlike viruses and worms, Trojan horses do not have the ability to self-replicate for spreading, therefore, they often combine with viruses and worms to infiltrate the user’s computer.
Spyware: This is software that monitors your activities on the computer. It collects all personal information, habits, and browsing behaviors of users and sends them back to the author. Spyware poses a significant threat to the safety of a computer or computer system.
 Adware: Simply put, this is a form of advertising software stealthily installed on the user’s computer or installed through free software that users permit (without being aware of their purpose). However, they do not stop at merely advertising; when combined with other types of viruses, they aim to increase the “destructive effectiveness”.
Adware: Simply put, this is a form of advertising software stealthily installed on the user’s computer or installed through free software that users permit (without being aware of their purpose). However, they do not stop at merely advertising; when combined with other types of viruses, they aim to increase the “destructive effectiveness”.
Worm: Computer worms are a type of software that spreads rapidly and widely, making them one of the most prevalent today. Unlike primitive viruses, worms do not need “bait” files to infect. They self-replicate and spread through the Internet, peer-to-peer networks, and file-sharing services…
Identifying Infected Computers
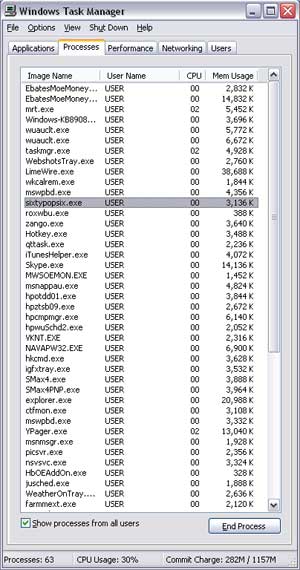
After infiltrating a system, some viruses immediately cause destruction. Others hide, quietly spreading to other computers, waiting for the right moment to launch a simultaneous “total attack,” catching users off guard; typical examples include the CIH and Melissa viruses. Common symptoms of a virus-infected computer include unusual signs such as continuous hard disk access; sluggish system performance; unfamiliar websites and automatic pop-up ads appearing while you work. If using Windows NT/2000/XP, you can check information in the Windows Task Manager, such as CPU Usage constantly at 100%, or the appearance of unfamiliar executable files in the Processes tab of the Windows Task Manager…
Virus Scanning
If you suspect your system is infected with a virus, you need to find software to check and eliminate them. Note: preventing viruses before they infiltrate the system is always simpler than eliminating them afterward. The article “New Virus Protection Weapons” introduces the 10 best antivirus products that can withstand both known and unknown threats. Each product has its strengths and weaknesses, ranging from free to paid, allowing you to choose the appropriate software for yourself.
Once you select suitable software, you need to install it on the system. Some “malicious” viruses can prevent users from installing or control these programs to avoid detection, blocking access to the manufacturer’s website. If you cannot install in Normal mode on Windows, try installing in Safe mode. To start your computer in Safe mode, do the following:
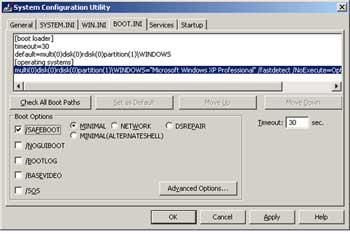
1. Use System Configuration Utility or press F8 during Windows startup to enter Safe mode.
– Close all running applications.
– Select Start. Run. Type msconfig and press Ok to open the System Configuration Utility window.
– In the BOOT.INI tab, check the /SAFEBOOT option under Boot Options.
– Click Ok and select Restart to confirm restarting the computer to enter Safe mode.
 Note:
Note:
To restart your computer in Normal mode: Follow the steps above and uncheck the /SAFEBOOT option under Boot Options.
Update the virus list. As mentioned above, if you cannot access the manufacturer’s websites and cannot update the virus definitions online, download them from another computer to update.
Disable System Restore. If using Windows ME or XP, you should turn off the System Restore feature when your computer is infected with a virus. By default, in Windows ME and XP, this feature is enabled to help you recover the system in case of issues. Antivirus software cannot scan the System Volume Information folder, where System Restore stores files and folders to recover the system. Therefore, a “reinfection” can occur when System Restore restores the archived versions that are infected with viruses.
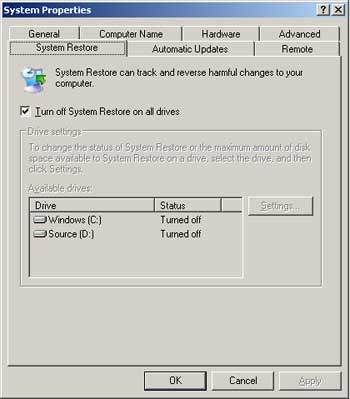
To disable System Restore in Windows XP, do the following:
– Right-click on My Computer, select Properties.
– In the System Properties window, go to the System Restore tab, check the option Turn off System Restore on all drives and click OK.
– Select Yes when prompted for confirmation.
If using Windows ME, do the following:
– On the Desktop, right-click on My Computer and select Properties.
– In the System Properties window, select Performance. File System. Troubleshooting.
– Check the option to Disable System Restore and click OK.
– Select Close and Yes to restart Windows.
 Note: Disabling System Restore means deleting all restore points. You should manually create a restore point when System Restore is re-enabled.
Note: Disabling System Restore means deleting all restore points. You should manually create a restore point when System Restore is re-enabled.
Perform a full system scan. The default settings of some antivirus programs only scan certain specified file types. To be thorough, you should set it to “full system scan” to ensure your computer is checked completely. Some notes during the scanning process:
– If you encounter an error message that the software cannot delete the virus or a specific virus file, restart your computer in Safe mode and continue the check.
– Upon completion of the scan, the program will provide a summary report of the detected viruses and how to handle them. If the program cannot eliminate certain types of viruses, try to remove them manually. Use a search engine with the virus’s name as the keyword, and you will find instructions on how to eliminate them on some antivirus software websites.
– After restarting Windows in Normal mode, if you encounter an error message like “Windows cannot find [FILE NAME]. Make sure you typed the name correctly, and then try again. To search for a file, click the Start button, and then click Search.” For example, with the virus W32.Lecna.A, you may see an error message about not finding the file iexplore.exe. These are the “remnants” left by the W32.Lecna.A virus even though it has been eliminated. To delete them, you need to find and remove the keys that this virus added to the Registry. We still advise readers to back up the Registry before you “touch” it. Refer to the article “Caring for and Maintaining the Windows Registry,” ID: A0502_90.
Choose Start. Run to open the DOS Prompt; type “regedit” to open the Registry Editor. If you encounter the error message “Registry editing has been disabled by your administrator,” refer to the information related to this error in the article “Internet Explorer Always Accesses Strange Websites,” ID: A0604_154.
Find and delete the keys related to spyware in the following branches:
– KEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRun. Delete the key “iexplore.exe” = “iexplore.exe” in the right pane.
– HKEY_LOCAL_MACHINESoftwareMicrosoftCurrentNetInf. Delete the key “hostid” = “[RANDOM NUMBER]” and “pid” = “[ENCRYPTED DATA]”
– HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlLsa. Delete the key “forceguest” = “0”
Exit the Registry Editor and restart your computer.
Update patches for the OS and software. Some viruses like W32.Blaster.Worm often exploit vulnerabilities in the Remote Procedure Call service of Windows NT/2000/XP to cause damage. If you use Microsoft software, you can update the patches from http://www.microsoft.com/downloads/Search.aspx?displaylang=en to prevent reinfection after scanning.
“Prevention is better than cure!” In the next article, we will provide readers with some tips and tricks to protect their computers in the era of Internet explosion and virus outbreaks…
Đông Quân
References
* http://service1.symantec.com/SUPPORT/nav.nsf/docid/1999041209131106
* http://www.symantec.com/avcenter/cybercrime/trojans_spyware.html?src=symsug_us#
I’m sorry, but it seems that there is no Vietnamese article provided for translation. Please provide the article you’d like me to translate, and I will be happy to assist you with that.




















































