The danger level of this malware lies not only in its ability to collect and eavesdrop on data but also in its capability to evade detection from antivirus programs.
Security firm Check Point has recently discovered a dangerous type of malware that has been used in various espionage attacks from China targeting key organizations in Southeast Asia. This malware is now being utilized by the Sharp Panda hacker group to target high-level government organizations in Southeast Asian countries, including Vietnam, Thailand, and Indonesia.
Check Point’s report indicates that the campaign employing this malware has been ongoing since late 2022 and continues into 2023. These attacks typically start with phishing attempts to collect login credentials for the targeted systems.
Infection Chain of the New Malware
According to Check Point’s findings, the Sharp Panda attack campaign begins with the use of phishing emails containing embedded malicious Docx files. Its mission is to deploy the RoyalRoad RTF kit onto the victim’s computer, seeking to exploit unpatched vulnerabilities to implant the malware.
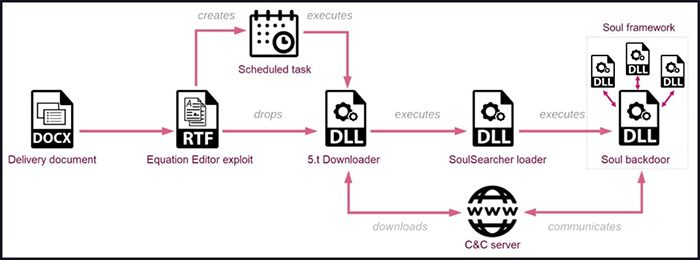
Attack process chain of Soul malware. (Image: Check Point).
In this case, the exploit will create a scheduled task, which then implants and executes a downloader to retrieve a malicious DLL file. This DLL file will subsequently be loaded into the system and will download a second DLL file named SoulSearcher from a C2 server.
The second DLL file will create a registry key, where the value will contain the final payload compressed, which can then be decompressed to load the Soul backdoor module into the RAM, allowing this malware to evade detection by commonly used antivirus tools on the compromised system.
Details on the Attack Methodology of Soul Malware
When executed, the main module of the Soul malware establishes a connection to the C2 server and awaits additional modules to expand its functionality.
In the new version discovered and analyzed by Check Point, this malware is equipped with a “radio silence” mode that allows malicious actors to refrain from communicating with the command server during certain time frames in the week—typically during the victim’s working hours—to avoid detection.
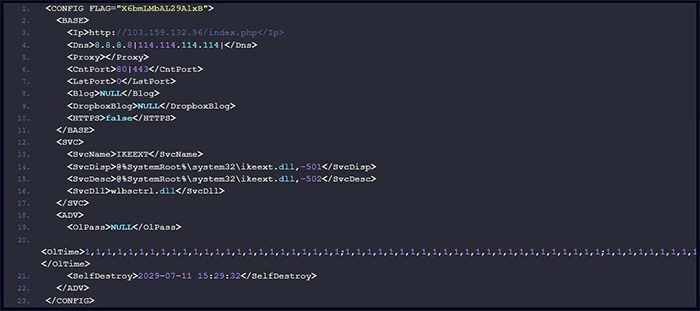
Main backdoor configuration of the malware. (Image: Check Point).
A representative from Check Point stated: “This is an advanced cyber attack feature that allows malicious actors to blend their communications with the device’s standard bandwidth and reduce the likelihood of detection within network communications.”
Furthermore, this new version also embeds a custom communication protocol with the C2 server, utilizing various HTTP query methods, including GET, POST, and DELETE.
These different HTTP query methods enable the malware to be more flexible and capable; for example, a GET query can be used to retrieve data while a POST query can be used to send data.
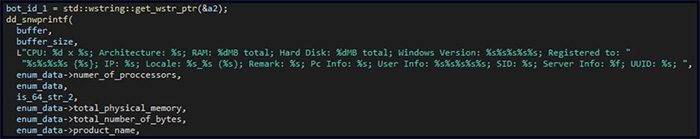
System data sent to the malware server, including hardware and operating system information. (Image: Check Point).
To establish communication with the C2 server, the Soul malware initially self-registers and sends the victim’s computer fingerprint data (including hardware details, operating system type, time zone, IP address) to the C2, after which it begins an infinite communication loop with this server.
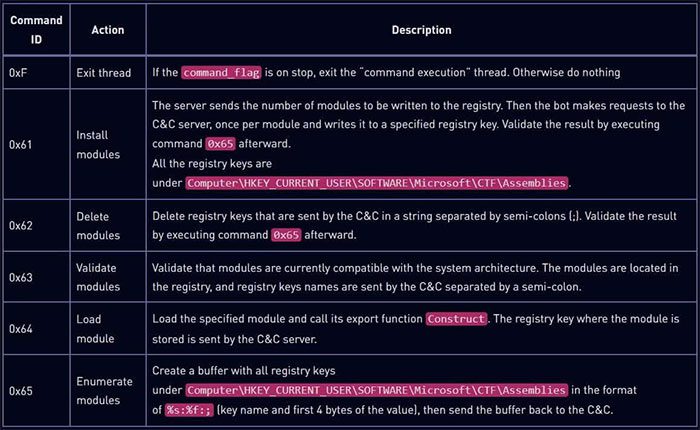
Functional commands supported by Soul malware. (Image: Check Point).
From this C2 server, the Soul malware will receive commands to download additional modules, collect and send back system hardware data, restart communication with the server, or terminate its operational processes.
Check Point was unable to obtain samples of these additional modules, but they believe they may perform various specialized functions, such as file manipulation, data filtering, keylogging, taking screenshots, and many other dangerous functionalities. This array of capabilities highlights the threat level of attacks using Soul malware for eavesdropping as it collects sensitive data from the infected computers. Even more alarming is its ability to evade detection by antivirus programs, allowing it to gather data over extended periods without being hindered.





















































