 There are currently many tools available to enhance computer security, but if you’ve tried using Invisible Secret 4, you’ll quickly appreciate its perfect security capabilities for everything it protects, even in cases where keyloggers are installed on the computer.
There are currently many tools available to enhance computer security, but if you’ve tried using Invisible Secret 4, you’ll quickly appreciate its perfect security capabilities for everything it protects, even in cases where keyloggers are installed on the computer.
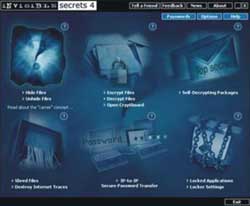
Invisible Secret 4 offers various features such as hiding folders, encrypting files, permanently deleting files beyond recovery, erasing all traces of applications accessed, IP security, locking applications, and more…
1. Hiding Folders
Select “Hide Files” -> go to Add files to choose the files to hide -> click Next to enter the name of the file to hide in the “Enter the file name…” box -> select the appropriate file type in the “Carrier type” box -> click Next and enter the necessary passwords, then choose an encryption algorithm such as: AES – Rijndael, Twofish, RC4, Gost, Cast128… -> Click Next and Hide to conceal the file. The hidden file will have the extension of the original file’s name.ISC.
During the “Add files” process, you should choose both the compress (Compress) and delete (Delete, Shred) options to significantly reduce the size of the hidden file, while the original file will be permanently deleted. You should also select the “New message” function to create a note for the file you want to hide.
To restore the hidden file to its original state, click on “Unhide Files” -> find the hidden file -> enter the necessary password to reveal the original file.
2. File and Folder Encryption:
Select “Encrypt Files”. Here you can encrypt individual files or an entire folder by clicking on “Add files” or “Add Folders” -> click Next to enter a password and select the encryption type, and finally click the “Encrypt” button to encrypt each file or the entire folder. The encrypted files will also have the .ISC extension and will be located in the same directory as the selected folder for encryption. If you want to decrypt the file or folder, select the “Decrypt Files” feature.
3. Permanently Deleting Files Beyond Recovery:
 |
|
Overwrite 9999 times for permanent deletion |
Select “Shred Files” -> go to “Add files” to choose the files to delete -> select “Shred” and click Yes to permanently delete the file. Invisible Secret 4 uses the “DoD 5220.22-M” file deletion technology from the U.S. Department of Defense, making deleted files nearly impossible to recover.
To clean up traces of internet access and applications while tidying up the computer, select the “Destroy Internet Trace” function to have Invisible Secret 4 completely erase all cache, cookies, and history of Internet Explorer, as well as remove traces of access from other applications. Be sure to check the “Use DoD…” box for Invisible Secret 4 to apply the “DoD 5220.22-M” technology for thorough deletion.
4. IP-to-IP Password Transfer:
This unique feature allows the owners of two computers to securely send each other any necessary passwords for decrypting files in Invisible Secret 4.
To receive a password, select the “Receive Password” box, then enter the IP address of the computer you are using -> click Next and wait for your friend’s password to be sent to your machine as a text message.
To send a password to your friend, select the “Transmit Password” box -> enter the recipient’s IP address and the password to be sent -> click Next for the two Invisible Secret 4 programs on both machines to connect via IP and complete the password transfer process.
5. Locking All Installed Applications:
Click on “Locked Applications” -> enter the required password -> select “Lock New Application” to display a list of all applications installed on the computer. Choose the applications to lock one by one by holding the Ctrl key and clicking once to select. Once you have finished selecting, click the “Lock” button. When the icon of the application to lock appears in the list, click “Finish” to complete the locking process for the selected applications.
If you pay close attention, you will notice that in the user interface of all features in Invisible Secret 4, there is a function button named “Virtual Keyboard”. When you click this button, a virtual keyboard will appear, allowing you to type the password by clicking on each character on the virtual keyboard. This feature will bypass any keylogger programs that may have been secretly installed on your computer without your knowledge.
To use the program most effectively, you should go to “Option” to learn and create your own settings. The most interesting feature is that you can choose to “annihilate” data completely by commanding Invisible Secret 4 to delete and overwrite any data in the deleted area up to… 9999 times, enough to discourage even the most powerful data recovery tools available today. Additionally, Invisible Secret 4 also provides an exceptionally effective password management feature (go to Option -> select the Password tab) regardless of how many passwords you have.
NeoByte Solutions is selling Invisible Secret 4 Version 4.4 for $39.95. Users can visit http://www.gold-software.com/InvisibleSecrets-file4092.html to download the trial version.
HOÀNG KIM ANH