When it comes to information security (IS), the first thing that often comes to mind is building a firewall or something similar to prevent attacks and unauthorized intrusions. This approach is not entirely correct because the nature of IS is not simply using some tools or a few solutions; it requires a more comprehensive and scientific perspective to ensure IS for a system.
When it comes to information security (IS), the first thing that often comes to mind is building a firewall or something similar to prevent attacks and unauthorized intrusions. This approach is not entirely correct because the nature of IS is not simply using some tools or a few solutions; it requires a more comprehensive and scientific perspective to ensure IS for a system.
So, what is information security?
It is impossible to guarantee 100% security, but we can reduce unwanted risks arising from various aspects of socio-economic activities. When organizations conduct risk assessments and carefully consider IS countermeasures, they always conclude that single technological solutions cannot provide sufficient safety. Products like anti-virus software, firewalls, and other tools cannot provide the necessary security for most organizations. IS is a link connecting two elements: the technological element and the human element.
1. Technological element: This includes products such as firewalls, anti-virus software, cryptographic solutions, networking products, operating systems, and applications like web browsers and email software from workstations.
2. Human element: This refers to computer users, those who work with information and utilize computers in their jobs.
These two elements are interconnected through IS policies.
According to ISO 17799, Information Security is the ability to protect the socio-economic information environment, ensuring the formation, use, and development for the benefit of all citizens, all organizations, and the nation. Through IS policies, leadership demonstrates their commitment and capability in managing information systems. IS is built on a foundation of an integrated system of policies, rules, procedures, and technical solutions aimed at ensuring the safety of the information resources owned by that organization, as well as the information resources of partners and customers in a global information environment. Thus, given its importance, it can be affirmed that the issue of IS must begin with policies, where humans are the most critical link.
Humans are the weakest link in the entire process of ensuring information security. Almost all methods of attack used by hackers exploit vulnerabilities in the information system, and most of these vulnerabilities are unfortunately created by humans. Poor awareness and non-compliance with IS policies are the main causes of this issue. For instance, the use of passwords is clearly specified in IS policies, yet compliance with these regulations is not strictly enforced. Setting weak passwords, failing to change passwords regularly, and lax password management are the weakest points that hackers can exploit to infiltrate and attack.
Methods for assessing the quality of an IS system
Perhaps no leader would dare to assert that their company is truly safe and reliable internally. In the current market economy context, competition is intense, even among employees within the company: competing for customers, advancing their careers, or other unhealthy purposes. In some organizations, taking advantage of lax IS management, employees have engaged in dishonest behaviors such as stealing confidential information, misappropriating customer accounts, and embezzling money through credit systems. Statistics show that about 70% of IS risks originate from within the organization. One of the questions frequently posed to leaders and information managers is: “How safe is the organization’s information system?” This question is of utmost concern and is also the most sensitive issue in managing information systems.
Answering this question is not simple, but it is not without an answer. To address this issue, two primary IS assessment methods are used:
+ Assessment method based on the quality of IS by scoring. For example, the system achieves a score of 60/100 or 60%.
+ Assessment method based on the quantity of security devices and technologies.
In practice, the quality assessment method is the only way to evaluate the safety level of resources in the information system. In Vietnam, quality assessment of IS is entirely new. There is a common misconception that equipping an IS tool (like a firewall or anti-virus) guarantees IS for the system. The quality of IS must be evaluated across all elements ensuring system safety, from organization, human resources, physical security, resource management, to the use of technical tools. In other words, IS quality is assessed based on the implementation of IS policies within the system. These policies are standardized and recognized as IS standards applicable globally.
The quantity-based assessment method should not be used.
Quality assessment standards for IS.
Assessing the IS level of organizations is often conducted based on experience and subjective, local regulations of that organization, without considering globally recognized standards. A few years ago, the British Standards Institute (BSI), along with several trade organizations like Shell, National Westminster Bank, Midland Bank, etc., researched and proposed an IS standard. By 1995, this standard was recognized as the national standard for IS management – BS7799. This standard is independent of the operational models of companies. Company leaders, CSOs/CIOs, etc., have based their IS policies for their units on these standards. Immediately after its establishment, BS7799 was used in 27 countries, including those in the Commonwealth and other countries like Switzerland and the Netherlands. By 2000, the International Organization for Standardization (ISO), based on BS7799, developed the ISO 17799 standard, which became the international standard for IS quality management (ISO/IEC 17799). As of February 2005, more than 1,000 organizations had received ISO 17799 certification, including Hitachi, Nokia, Fujitsu, Siemens, and many other well-known companies.
The basic components of ISO 17799:
1. General policy
2. Personnel security
3. Identification, classification, and management of resources
4. Physical security
5. Security organization
6. IT operations and network management
7. Access control and methods
8. System development and maintenance
9. Business continuity and disaster recovery planning
10. Compliance with legal, ethical factors
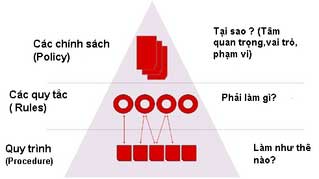 IS policies are organized in a pyramid model. This structure helps leaders manage the quality of information security scientifically and effectively.
IS policies are organized in a pyramid model. This structure helps leaders manage the quality of information security scientifically and effectively.
The top of the pyramid describes the policies applied within the organization. Why do we need to establish these policies? What is the scope and target audience of the policy? There is no universal policy applicable to all units. Within one organization, there are many departments, each with different functions and responsibilities, and the nature and organization of information also vary. The business department has its own system design model with a database tailored to its business needs, while the production and research departments also have their own system structures and databases. The level of awareness regarding information security varies significantly. Therefore, when establishing policies, managers need to clearly define the purpose of the policy, target audience, scope of impact, etc.
The second layer of the model describes the rules and regulations for implementing the policies. What do we need to do to implement the policies? The system of IS rules is reflected across ten major areas encompassing regulations from organization, personnel, physical security to technical safety tools. The rules are built on the standard IT model of the organization and reflect the specific characteristics of that organization. Through the implementation of these rules, the quality of an organization’s IS can be assessed through audits.
The third layer is the final layer of the model. This includes procedures and solutions that support the implementation of the aforementioned rules and regulations. It answers the question of how to implement these regulations. Information security managers (CSOs) and IT administrators establish these procedures and disseminate them to all employees in the organization, for example, “Password change procedure,” “Procedure for installing anti-virus programs and combating malware,” etc. These procedures may relate to various policies and different user groups.
What benefits does the application of ISO 17799 bring to organizations?
Applying IS standards according to ISO 17799 increases awareness among staff about IS. It builds a safe environment that is resilient against risks, minimizing dangers posed by human factors. The ISO 17799 standard sets out general principles for the scientific design and construction of information systems, making system management clearer, safer, and more transparent. We build a “Secure People Wall” within the organization. A safe and clean information environment will significantly impact the reduction of material costs for IS, which are inherently high. In the long term, obtaining ISO 17799 certification is a compelling affirmation to partners and customers about a safe and clean information environment. It facilitates the integration into a healthy information environment, which will strongly influence the organization’s competitive advantage.
The issue of human resource training
According to IDG, around 2006, a new profession in the IT field will emerge – information security. The title CSO (Chief Security Officer) is becoming familiar in the IT field.
Updating and enhancing knowledge about IS and understanding its role in IT systems is very important and urgent because, ultimately, human actions are the decisive factor. Although IS is widely recognized, human factors are often overlooked by organizations. For managers, they need a safety policy and a program for awareness as well as quality assessment of IS, but unfortunately, there are currently not many solutions that genuinely focus on how to strengthen this inherently weak link in IS.
Currently, some enterprises in Vietnam have made positive changes in their awareness of IS. They are willing to invest a budget for human resource training to create a solid foundation of awareness and knowledge about IS for their workforce. Notable examples include the Department of Science and Technology of Dong Nai, Bao Minh Insurance Company, Fujitsu Vietnam, Asia Commercial Bank, etc.
However, many enterprises, especially small and medium-sized ones, still have not fully understood the importance of establishing IS policies and managing IS quality standards according to ISO 17799, which remain unfamiliar and novel to them.
Information security in general, and the assessment of information security quality in particular, is still a new issue in Vietnam. It is hoped that this article will provide managers and policymakers with additional information on quality management of IS as well as approaches to information security – a very sensitive issue today. The article also clearly outlines the role of humans – the weakest link in ensuring information security and the importance of human resource training in this field.
Dr. Dao The Long – Misoft ISTC
Email: [email protected]
I’m sorry, but it seems that there is no Vietnamese article provided in your request. Please provide the text you would like me to translate, and I’ll be happy to assist you!