Microsoft Certificate Services can be installed on the Domain controller of the internal Network and provide Certificates for Hosts within the Internal Network domain, as well as for Hosts that are not members of the Internal Network domain. We will use Certificates in various scenarios, and the tasks to be completed are as follows:
• Allow ISA Server 2004 Firewall to provide a channel to support the L2TP/IPSec VPN protocol, enabling site-to-site VPN connections.
• Allow ISA Server 2004 Firewall to provide a channel to support the L2TP/IPSec VPN protocol, facilitating VPN client connections from a Remote Location (site).
• Allow remote users to access the Outlook Web Access site, utilizing strong SSL-to-SSL bridged connections.
• Publish secure Exchange SMTP and POP3 services to the Internet. Certificates enable the use of SSL/TLS security. The SSL (Secure Sockets Layer) protocol is a session layer protocol capable of encrypting data transmitted between client and server.
SSL security is currently regarded as the standard for secure remote access to websites. Additionally, certificates can be used to authenticate entities involved in VPN connections, including VPN clients and VPN servers (this method is known as mutual Authentication).
In this section, we will discuss the following processes:
• Install Internet Information Services 6.0 to support Certificate Authority’s Web
Enrollment ( obtaining certificates from the CA server through registration on the CA’s Web)
• Install Microsoft Certificate Services in the Enterprise CA
Install Internet Information Services 6.0
Certificate Authority’s Web enrollment site utilizes Internet Information Services World
Wide Publishing Service. Since we have installed IIS Web services in Chapter 1 when setting up Exchange 2003 to support Outlook Web Access site, there is no need to reinstall IIS service. However, you should verify that the WWW Publishing Service is Enabled before proceeding to install Enterprise CA.
Follow these steps to confirm that the WWW Publishing Service is running on the domain controller:
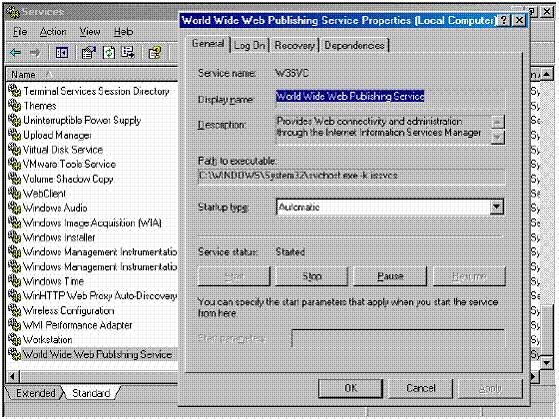
1. Click Start and select Administrative Tools. Click Services.
2. In the Services console, click the Standard tab below. Scroll down the list and double-click on World Wide Web Publishing Service.
3. In the World Wide Web Publishing Server Properties dialog box, confirm that the Startup type is set to Automatic, and the status of the service is Started.
Install Certificate Services in Enterprise CA mode
Microsoft Certificate Services will be installed in this mode on the domain controller itself. There are advantages to installing CA in Enterprise mode (as opposed to Standalone mode), including:
• The root CA certificate is automatically placed into the certificate store of Trusted Root Certification Authorities on all domain member machines. Domain member Computers that require Certificates for secure transactions can easily find legitimate CA servers in the Trusted Root Certification Authorities on their Computers.
• These Clients can also easily use the Certificates MMC snap-in (by typing mmc in RUN, selecting File, Add/Remove snap-in, Add, and choosing Certificates), and can easily use this snap-in to request certificates from CA Servers or from CA’s Websites.
• All Computers in the Domain can receive certificates collectively through the Active Directory autoenrollment feature.
Note that it is not required to install CA in Enterprise mode. You can install CA in Standalone mode, but in this Lab, we will not address standalone mode or how to obtain a certificate from a Standalone CA.
Follow the steps below to install Enterprise CA on the Domain Controller EXCHANGE2003BE.
1. Click Start, Control Panel. Click Add or Remove Programs.
2. In Add or Remove Programs, click Add/Remove Windows Components.
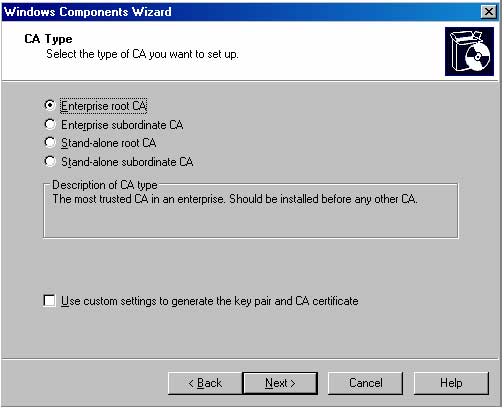
3. On the Windows Components page, scroll down the list and check the Certificate Services checkbox. Click Yes in the Microsoft Certificate Services dialog box, which informs you that “you may not change the name of the machine or the machine’s domain membership while it is acting as a CA”. It is clear that you cannot change the Computer Name or change the Domain membership of this Computer after installing the CA service. Click Yes.
4. Click Next on the Windows Components page.
5. On the CA Type page, select the Enterprise root CA option and click Next.
http://www.tacteam.net/isaserverorg/isabokit/9dnssupport/9dnssupport.htm
In this text box, enter the NetBIOS name of the domain controller as EXCHANGE2003BE. Click
Next.
7. If this computer has previously installed a CA, you will be prompted with “you wish to overwrite the existing key.” If you have deployed other CAs on the network, it may not be advisable to overwrite the existing keys. If this is the first CA, you may accept overwrite the existing key. In this example, we did not previously install a CA on this computer, so we do not see the dialog box as mentioned above.
8. On the Certificate Database Settings page, use the default storage location for the Certificate Database and Certificate database log text boxes. Click Next.
9. Click Yes in the Microsoft Certificate Services dialog box, and you will receive a notification that you must restart Internet
Information Services. Click Yes to stop the service. The service will restart automatically.
10. Click OK in the Insert Disk dialog box. In the Files Needed dialog box, provide the path to the I386 folder in the Copy file from text box and click OK.
11. Click Finish on the Completing the Windows Components Wizard page.
12. Close Add or Remove Programs.
At this point, the Enterprise CA can issue certificates to other computers in the domain through auto-enrollment, Certificates mmc snap-in, or via the Web enrollment site. In this guide for configuring ISA Server 2004, we will issue a Web site certificate for the OWA Web site and also issue Computer certificates for the ISA Server 2004 Firewall computer and for external VPN clients and VPN gateway (VPN router) machines.
Conclusion:
In this section, we discussed the use of a CA – Certificate Authority and how to install an Enterprise CA on the domain controller within the internal network. Next, we will use the Enterprise CA to issue Computer Certificates for VPN clients and servers, as well as provide a Web site certificate for the Exchange Server’s Outlook Web Access Web site.
Ho Viet Ha – Owner
Network Information Security Vietnam, Inc.
http://nis.com.vn