CHAPTER 3: Installing and Configuring Microsoft Internet Authentication Service
 Microsoft Internet Authentication Service (IAS) is a type of RADIUS (Remote Authentication Dial In User Service) server used to authenticate users connecting to the ISA Server 2004 Firewall machine. IAS can be used to authenticate Web Proxy clients on the internal network or VPN clients and VPN gateways connecting from an external network location (for example, from a branch office of the company). Additionally, RADIUS can authenticate remote users when they connect to web servers published through Web Publishing rules on ISA Server 2004.
Microsoft Internet Authentication Service (IAS) is a type of RADIUS (Remote Authentication Dial In User Service) server used to authenticate users connecting to the ISA Server 2004 Firewall machine. IAS can be used to authenticate Web Proxy clients on the internal network or VPN clients and VPN gateways connecting from an external network location (for example, from a branch office of the company). Additionally, RADIUS can authenticate remote users when they connect to web servers published through Web Publishing rules on ISA Server 2004.
The main advantage of using RADIUS to authenticate Web Proxy and VPN connections is that the ISA Server 2004 Firewall computer does not need to be a member of the Active Directory Domain to authenticate users whose accounts are in the Active Directory database on the internal network. Many firewall administrators recommend that the firewall computer should not be a member of the domain. This can prevent attackers from gaining access to the firewall and obtaining domain member rights from this firewall, thus expanding their attack vector into the internal network.
However, a significant drawback of not making the ISA Server 2004 Firewall a member of the internal network domain is that we will not be able to use the ISA Firewall Client to provide legitimate authentication for the ISA Server when these firewall clients access all TCP and UDP protocols. For this reason, we will create an ISA Server 2004 Firewall computer as a member of the internal domain. However, if you do not join the firewall to the domain, you can still use IAS to authenticate VPN and Web Proxy clients.
The subsequent tasks will be:
Installing and Configuring Microsoft Internet Authentication Service
The Microsoft Internet Authentication Service server is a RADIUS server. We will use this RADIUS server in the following sections of this guide (enabling RADIUS authentication for Web Publishing Rules and understanding how a RADIUS server authenticates clients).
Follow these steps to install Microsoft Internet Authentication Server on the domain controller EXCHANGE2003BE in the internal network:
1. Click Start, Control Panel. Click Add or Remove Programs.
2. In Add or Remove Programs, click Add/Remove Windows Components.
3. On the Windows Components page, scroll down the Components list and select the Networking Services entry. Click Details.
4. Check the Internet Authentication Service checkbox and click OK.
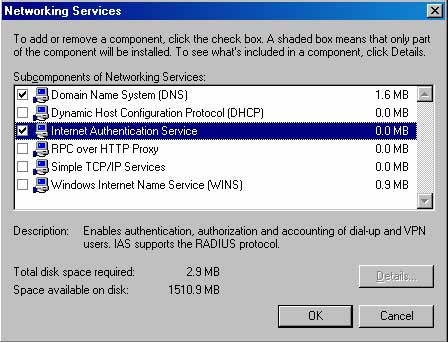
5. Click Next on the Windows Components page.
6. Click Finish on the Completing the Windows Components Wizard page.
7. Close Add or Remove Programs.
Next, we will configure the Internet Authentication Service.
Configuring Microsoft Internet Authentication Service
You need to configure the IAS server correctly to work with the ISA Server 2004 Firewall computer. At this point, we will configure the IAS Server to work with the ISA Server 2004 Firewall. Then we will configure the firewall to communicate with the IAS server.
Follow these steps on the Domain controller in the internal network to configure the IAS server:
1. Click Start, Administrative Tools. Click Internet Authentication Service.
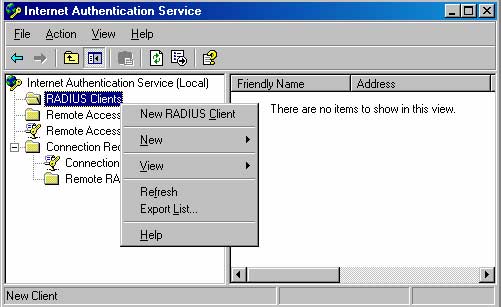
2. In the Internet Authentication Service console, expand the Internet Authentication
Service (Local) node. Right-click on the RADIUS Clients node and click New RADIUS
Client.
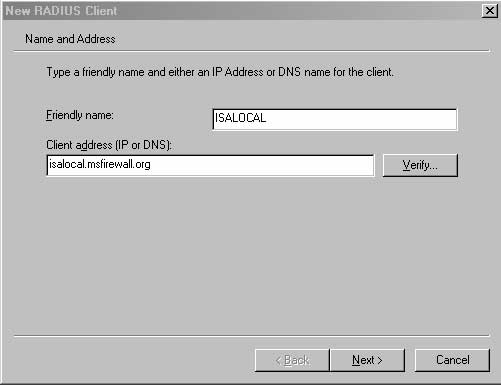
3. On the Name and Address page of the New RADIUS Client wizard, fill in the Friendly-name of the ISA Server 2004 Firewall computer in the Friendly name text box. This name is simply used to identify the RADIUS client and is not used for operational purposes. Enter the full FQDN name (which is EXCHANGE2003BE.MSFIREWALL.ORG), or the IP address of the ISA Server 2004 Firewall computer in the Client address (IP or DNS) text box.
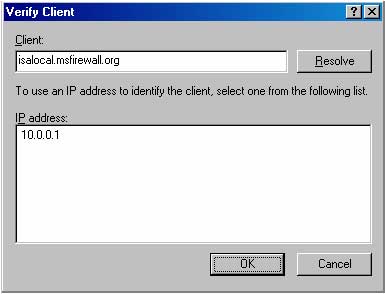
4. Click Verify. In the Verify Client dialog box, the FQDN – fully qualified domain name of the ISA Server 2004 Firewall computer will appear in the Client text box. Click Resolve. If the RADIUS server can resolve the name, the IP address will appear in the IP address frame. If the RADIUS server cannot resolve the name to an IP address, this indicates to the Admin that the hostname of the ISA Server 2004 Firewall has not been created in the DNS server (the record for the ISA Server has not been created). In this case, you can provide two solutions: Create an A Record for the ISA Server on the DNS server installed on the Domain Controller, or you can use the IP address on the Internal interface (10.0.0.1) of the ISA Server 2004 Firewall in the Client address (IP and DNS) text box on the Name or Address page (as mentioned above). Click OK in the Verify Client dialog box. The purpose of the settings in this section is to turn the ISA Server 2004 Firewall into a RADIUS Client, which allows the RADIUS server and the new RADIUS Client to collaborate.
5. Click Next on the Name and Address page of the New RADIUS Client wizard.
6. On the Additional Information page of the wizard, use the default Client-Vendor entry, which is standard for RADIUS. Enter a password in the Shared secret text box and confirm this password . The shared secret password (known only to the RADIUS server and RADIUS Client – ISA Server 2004 Firewall) is used for their communication. The Shared Secret must contain at least 8 characters (including uppercase, lowercase, numbers, and special characters). Check the Request must contain the Message Authenticator attribute checkbox. Click Finish.
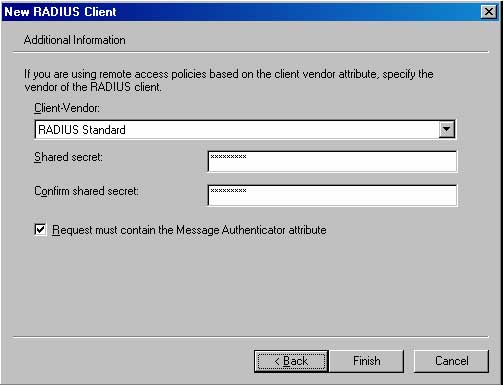
7. Now you will see the New RADIUS client entry appear on the console.
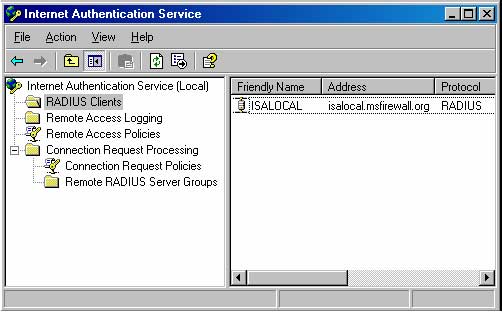
8. Close the Internet Authentication Service console.
The next configuration on the ISA Server 2004 Firewall to recognize its partner as the RADIUS server will be done through the ISA Server 2004 Firewall management interface. This RADIUS server will handle the authentication of requests from web and VPN clients.
Conclusion:
In this chapter, we discussed Microsoft Internet Authentication Server, how to install and configure an IAS server on the Domain Controller within the Internal Network domain. In the following sections of the guide, we will use this IAS server to authenticate requests from external sources (incoming requests from Web/VPN Clients) accessing the Web/VPN server.
(Stay tuned for Chapter 4..)
Previous Chapter:
Installing and Configuring ISA Server Firewall 2004 – Chapter 2: Installing Certificate Services
Ho Viet Ha – Owner
Network Information Security Vietnam, Inc.
http://nis.com.vn
Email: [email protected]




















































