In the past two days, a series of Denial of Service attacks have continuously targeted the address www.hvaonline.net, causing the HVA hacker association forum to be completely paralyzed.
 |
|
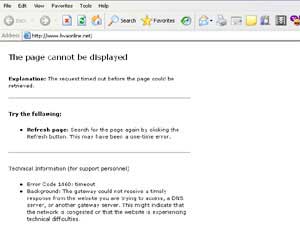
Screenshot of hvaonline.net taken at 4:15 PM on December 1 |
Yesterday, if you accessed this website, the only message displayed was: “The page cannot be displayed“. Currently, HVA has restored its services and the website is functioning normally.
A member, who wished to remain anonymous, from HVA’s management stated that it is common for hackers to use various tricks and methods to undermine this forum. However, this particular denial of service attack is reported to be twice as damaging as the most recent one.
“The evidence we have indicates that the perpetrator used a method called ‘xflash’. This involves secretly placing a banner with pre-installed attack code on several high-traffic websites“, described a representative from HVA. “As a result, each visitor to these websites automatically downloaded the attack code and unintentionally became a conduit for valid commands directed at HVA’s server“.
This individual also revealed that while previous disruptive campaigns operated at a level of 10,000 SYN packets per second, this attack reached approximately 16,000 SYN packets per second. “It is rare for any server to be strong enough to withstand such a powerful and continuous ‘blow’“, stated the HVA representative.
Currently, HVA members are still unaware of the identity of the attackers and are continuing to analyze the code to investigate further. However, the source of the attack has been traced to a free server located in Japan.
Denial of Service (DDoS) attacks are currently regarded as the number one threat to cybersecurity and are a nightmare for websites due to the limited ability to defend against them. Many have openly expressed the view that this is one of the most reprehensible tactics among the various forms of online sabotage.
Nguyễn Hằng