Recently, we have received numerous inquiries from system administrators managing Domain Controllers on Windows Server 2003. They have lost the login password for their DC 2003, which controls the entire functionality of Active Directory Domain 2003. This unfortunate situation can occur when an admin periodically changes the password to enhance system security but, for some reason, forgets the new password. As a result, they can no longer log on to their Domain Controller and did not create any backup admin accounts as a precaution against forgetting the password.
Several tricks and tools that were published to reset the Domain Admin Password on Windows 2000 Server are no longer effective on Windows 2003 Server. The reason is that Microsoft has significantly strengthened the security features on Windows 2003 Server, rendering those tricks ineffective.
Below, we will present a method for resetting the Domain Admin Password account. Before proceeding, please pay close attention to all the mandatory requirements below:
Warning: This guide is intended solely to assist admins in resolving issues they have caused themselves. It is not intended for any malicious purposes to infiltrate a system!
Mandatory Requirements:
You need to meet the following requirements:
1/ Local access to the Domain Controller (DC) server.
2/ Access to the Local Administrator password (this is the Active Directory Restore mode password you set during the process of upgrading a Server 2003 to a Domain Controller 2003; this password is completely different from the password controlling the operations of the DC and Domain that you have forgotten).
3/ Two tools provided by Microsoft in the Resource Kit: SRVANY and INSTSRV. Download them here: http://www.microsoft.com/downloads/details.aspx?FamilyID=9d467a69-57ff-4ae7-96ee-b18c4790cffd&DisplayLang=en
All these steps are carried out on a domain with a Domain Controller 2003. If your domain has multiple DCs, you can choose any Domain Controller to perform the steps.
Procedure:
1. Restart the DC Windows 2003 in Directory Restore Service Mode.
Restart the machine, and at startup, press F8 and select Directory Restore Service Mode. In this mode, Active Directory functionality will be disabled.
When the login screen appears, log on with the Local Administrator account. You will have full access to this Local Computer but cannot intervene in any issues related to Active Directory.
2. Proceed to install SRVANY.
This utility runs as a Windows NT Service. The interesting aspect here is that the program will have SYSTEM privileges, which are necessary to reset the Domain Admin password. You will configure SRVANY to launch the command prompt (which will allow you to run the net user commands).
Copy SRVANY and INSTSRV into a temporary folder, for example, d:temp. Also, copy cmd.exe into this folder (cmd.exe is the command prompt, usually located at %WINDIR%System32, e.g., C:WindowsSystem32).
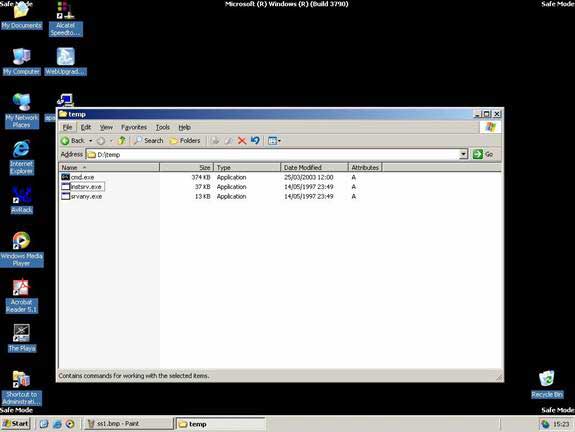
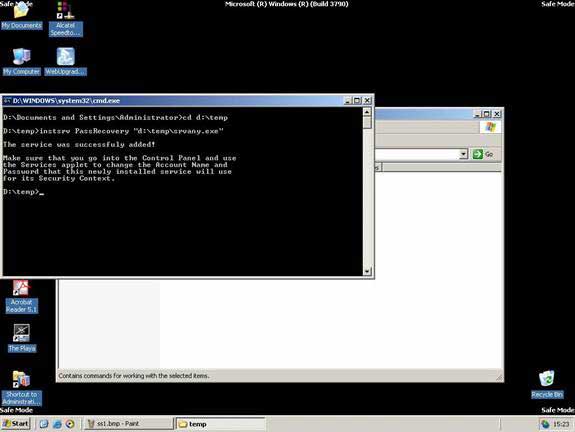
Click on cmd.exe to launch the command prompt, type the command Cd D:temp and press Enter, then type the command instsrv PassRecovery “d:tempsrvany.exe” and press Enter.
Configure SRVANY.
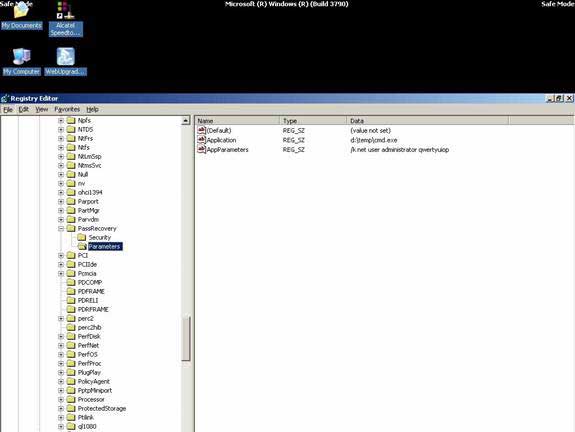
In Run, type the command regedit, open the Registry Editor, and navigate to the Key
HKEY_LOCAL_MACHINESystemCurrentControlSetServicesPassRecovery
Right-click on the key PassRecovery and create a subkey Parameters, then add the following two new values:
name: Application
type: REG_SZ (string)
value: d:tempcmd.exe
name: AppParameters
type: REG_SZ (string)
value: /k net user administrator new_password
Be Careful: ‘net user username password‘ is the command line to set a new password. Replace new_password with the actual password you want to set. Keep in mind that some domain policies may require you to set complex passwords, so the password must include uppercase letters, lowercase letters, numbers, and special characters, e.g., p@ssW0rd!#$
Next, in Run, type the command Services.msc or go to Control Panel -> Administrative Tools > Services, which will open the control panel for the services running on the system. Look for the service named PassRecovery, right-click and select the property tab. Ensure the start mode is set to Automatic.
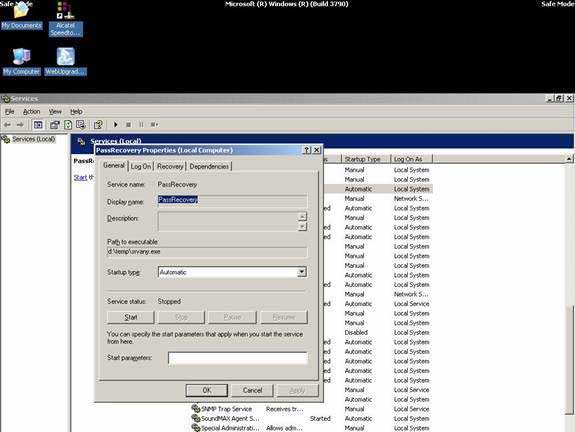
Open the Log On tab and check the option Allow service to interact with desktop.
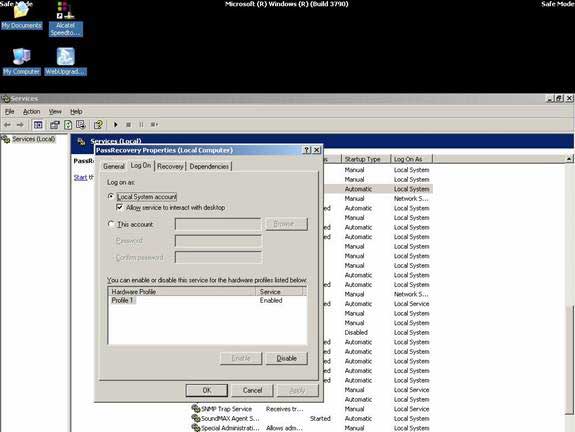
At this point, you can restart Windows, and SRVANY will execute the net user command to reset the domain admin password.
3. Restart Windows in normal mode
Wait for the login screen to appear. You will not see the command prompt appear when executing the net user command. But don’t worry, the command is still executed in the background.
Log on with the Administrator account and the password you just set above. The system will grant you full access. If not, return to step 2 and ensure you have not forgotten the new password set or incorrectly set the other values.
When the desktop appears, you will see the command prompt. The command prompt was launched by SRVANY.
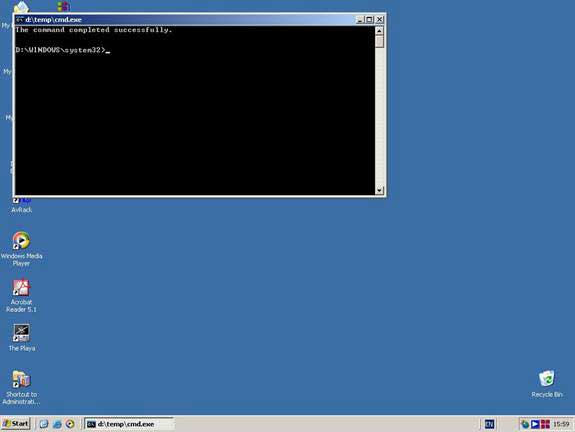
At this point, the goal has been achieved; proceed to remove SRVANY:
Execute the commands:
net stop PassRecovery
sc delete PassRecovery
Then delete the folder d:temp that was created. Finished!
Ho Viet Ha – Network Information Security Vietnam.
http://nis.com.vn
Email: [email protected]


















































