Spam: A Growing Issue on the Internet
 |
Phishing Activity Statistics |
Predictions for some new trends in spam in 2006 hope to help readers mitigate unnecessary damages.
Spam: A Long-term Battle
Spammers adapt quickly to countermeasures. Advertisements can originate from a server in Shanghai or from a regular computer in Detroit. All measures taken by spammers aim to deceive and bypass ISP controls.
However, 2005 was considered a successful year in the fight against spam. The number of blocked emails was quite substantial, about several tens of percent, with some ISPs reporting that they blocked over 90% of spam reaching users’ inboxes.
Nothing is permanent, and the world of spam prevention is expected to be fierce and challenging in the new year. The following predictions indicate some trends in the development of spam.
Increase in Volume
Experts refer to computers that are remotely controlled to distribute spam as Zombie computers. Currently, there is only a presence of individual Zombie computers, but 2006 promises to see a network of Zombie machines. This way, spammers will save costs and remain more anonymous.
In 2004, 35% of spam originated from Zombies; in 2005, this number rose to 60%, and it is predicted that in 2006, it will only increase.
New Scams
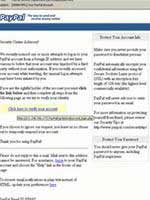 |
Fake Paypal |
Phishing refers to scams targeting individuals to gather personal information for financial purposes. The methods are diverse, ranging from impersonating well-known websites like Paypal and eBay to more sophisticated techniques like spear phishing, which impersonates close acquaintances such as colleagues, family, or friends.
Another method involves sending “special” requests, for example, notifying you that your account information has been compromised, providing you with a link to a website containing your information. When you panic and click the link, you fall victim to the scam. Many methods primarily target the greed and desires of the majority of Internet users.
The essence of these methods is still to trick you into clicking a link. If you fall for it, your computer will automatically download malicious code and programs, potentially turning your machine into a Zombie.
New Avenues
At the beginning of January, viruses began spreading through AIM (American Online’s instant messaging program) messages. These messages come from people you know (in your contact list), inviting you to view a picture on Myspace.com. Simply clicking the link will automatically download spyware, adware, and spam onto your machine.
Spread through security vulnerabilities in programs, especially those running on Microsoft Windows, will continue to develop, as no program is truly perfect.
A New “Look” for Spam
 |
SplogSpot |
Changes occur faster than fashion trends. In 2005, many spam scams offered free iPods or similar promotions.
However, in 2006, the focus will primarily be on financial and investment solicitations because they are harder to detect as forgeries.
Today, spam is not limited to emails; it also appears in blogs, known as spam blogs or splogs, and in online messaging. These trends are expected to flourish in 2006. Moreover, anti-spam laws and increasingly strict spam filters will force spammers to change their targets. That’s a long story.
The splog issue causes significant damage to blog service providers. There are websites dedicated to combating splogs, such as SplogSpot and Splog Reporter, where you can find more details.
Spam continues to cause economic harm to the Internet every minute. There will never be an end to the fight against spam. Depending on the awareness of Internet users and the strength of technology, it can only be partially limited…
TRẦN HUY




















































