Why is DDoS— a form of denial-of-service attack that even legitimate hackers no longer acknowledge—becoming increasingly common and a weapon so dangerous that it is nearly indefensible? Among various reasons, one heartbreaking truth is that DDoS emerges from the very negative ambitions of individuals to control and manipulate information.
 “Human is error”
“Human is error”
After many years of working in the infosec field, with countless joyful and sorrowful memories, the only thing that leaves me feeling unfulfilled in my career is the “DDoS monster.” Ultimately, all complex issues on the Internet stem from humanity. We have allowed our egos to lead us, facilitating and nurturing this monster.
One day, it will destroy the largest and most useful communication system we currently possess. The ancient saying, “Human is error,” is painful but profoundly true!
An Imperfect Internet
Even now, the Internet still carries flaws from its inception—flaws from the design process of the Internet. Some flaws arise from limited foresight and bias, while most are created either inadvertently or intentionally by humans:
Americans impose free speech—The Internet is completely anonymous
It’s hard to believe that a system with over 1 billion users has no mechanism for user identification!
This means that the very design of the Internet does not require users to authenticate themselves when using it. Want to use the internet? You just need to sit at any connected computer and use it. The Internet doesn’t care about your identity, fingerprints, or anything else about you!
 Very few people dare to run into the street and steal something from someone else. However, on the Internet, they are very confident in committing wrongdoing because they know the Internet protects them!
Very few people dare to run into the street and steal something from someone else. However, on the Internet, they are very confident in committing wrongdoing because they know the Internet protects them!
In my opinion, if they wanted to, the Americans could create a safer Internet by “forcing” all users to authenticate their identities before usage. Technically, this could be implemented quite easily; you can imagine that before using the Internet, you would need to provide a fingerprint to activate the network interface!
The Americans don’t care about this issue because they cherish free speech and impose the characteristic of free speech across the entire Internet. Humanity uses the anonymous Internet, and they are very confident to speak freely. However, in anonymity, people become very wild and display their primal characteristics. They attack each other, rob, and so on.
Technically, communication on the Internet is purely direct. A communicates with B without needing permission from C; the very design of the Internet supports this, and any efforts by C to control information can be easily neutralized. You can see this with websites blocked by firewalls from ISPs, which can easily be bypassed using numerous proxies on the Internet or tunneling techniques. The Internet is designed, managed, controlled, and exploited by Americans, and they have the ability to impose their will!!!
Humanity Acts Locally—The Internet Lacks Coordination
There are many technical issues of the Internet that are easy to solve, but we fail to address them because we act locally.
A typical example is the issue of IP address spoofing. If the ability to spoof IP addresses were eliminated, it would solve about 80% of the anonymity problem and other issues of the Internet.
 The technical requirement to eliminate the issue of IP address spoofing is that each network owner must filter and control packets leaving their network and exclude packets with inappropriate source addresses. This task takes five minutes; it’s just a matter of adding a few lines to the access list of the border router. For over twenty years, the issue of IP address spoofing has remained unresolved! Simply because IP address spoofing does not directly impact the network owner—typical “ignore it” mentality.
The technical requirement to eliminate the issue of IP address spoofing is that each network owner must filter and control packets leaving their network and exclude packets with inappropriate source addresses. This task takes five minutes; it’s just a matter of adding a few lines to the access list of the border router. For over twenty years, the issue of IP address spoofing has remained unresolved! Simply because IP address spoofing does not directly impact the network owner—typical “ignore it” mentality.
What will happen if countries do not coordinate with each other to address the problems of the Internet? Some systems in country X are used by hackers from country Z to attack networks of country Y; how will these countries collaborate? How can they punish the hacker’s actions without an agreement on the law??! Currently, there has been virtually no progress from countries in preparing for such scenarios!
The Nature of the DDoS “Monster”
A DDoS attack is not technically complex. The simple definition of a DDoS attack is: “It is a type of attack that brings a service-providing system to the brink of resource exhaustion or creates logical confusion that causes the system to stop functioning.”
I won’t delve too deeply into the nature of DDoS, but I want to compare two classic forms and the new form of DDoS known as Flash-DDoS.
Classic DDoS
The key issue for hackers attacking using the classic form is to gain control of as many computers as possible; then they will directly launch mass attacks remotely through a control channel. With a scale of attack networks comprising hundreds of thousands of machines, this form can instantly take down any system. Coupled with the ability to spoof IP addresses, this type of attack is very difficult to trace back.
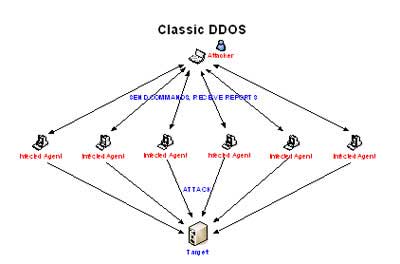 |
Classic DDoS Model |
This model has several drawbacks:
– The attack network is fixed, and attacks occur simultaneously, making it easy to trace back clues.
– The software installed on the infected agents is identical and can be used as evidence to convict the hacker.
– The victim can adjust their defense system to prevent attacks because the attack network is “visible.”
– Hackers must directly connect to the attack network at the time of the attack to control it, making it easy to track the perpetrator.
Flash-DDoS
Exploiting the popularity and the ability of the Flash player (which is almost present in every browser on the Internet today) to act as a web client, hackers have “improved” the classic DDoS model.
Hackers place a Flash file on a popular intermediary website; when users access this site, the Flash file is downloaded to their machines and executed by the Flash program. From here, countless requests will be sent to the target website.
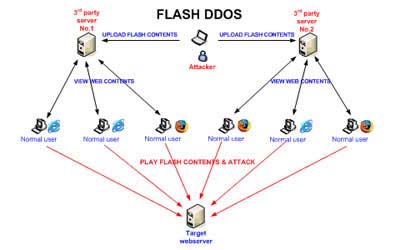 | |
Flash DDoS Cannot Be Stopped! |
Flash DDOS has certain characteristics that make prevention and detection almost impossible:
– Complex and self-forming attack networks:
+ It is not necessary to gain control and install DDOS software on infected agents. Instead, every user with a browser that supports Flash content (with Flash player) becomes a tool for attack.
+ The number of attack agents depends on the number of users accessing third-party websites that hackers have embedded Flash content into. This number changes over time and it is completely impossible to identify the source IP addresses, as these are regular users.
+ There is no process for sending commands and receiving reports between the hacker and the attack network; all attack commands are “embedded” in the Flash content, and the hacker does not need to receive reports since this is an asynchronous attack model.
+ Asynchronous attacks: The attack occurs without the need for commands. Users access third-party websites, load Flash content into their browsers, and when the Flash player executes the Flash content, their machines immediately become attack agents—continuously sending hundreds of requests to the victim’s web server.
 + The scale of the attack depends on the number of exploited third-party websites and the number of users frequently accessing these websites. For example, if a hacker exploits 10 third-party websites and each website has about 100 users accessing it at a time, the total number of requests that the victim’s server has to endure at a given moment can reach several tens of thousands!!! This is horrifying data for anyone managing the systems of any website, and the result is often an immediate system crash!
+ The scale of the attack depends on the number of exploited third-party websites and the number of users frequently accessing these websites. For example, if a hacker exploits 10 third-party websites and each website has about 100 users accessing it at a time, the total number of requests that the victim’s server has to endure at a given moment can reach several tens of thousands!!! This is horrifying data for anyone managing the systems of any website, and the result is often an immediate system crash!
Preventing Flash-DDOS is extremely difficult. Why is that?
+ It is impossible to distinguish between attack requests and normal requests to the system. When the number of requests to the system is very large, the administrator will need to “filter out” some attack requests; however, they will encounter difficulties in “finding and eliminating” attack requests.
+ Attacks come from all directions: with a flexible attack network, it is almost impossible to identify attack requests from source IP addresses.
+ All technical security measures face a practical limitation—that is, the resources of all systems are finite. When processing requests, these measures will consume system resources; when the number of requests is very large, the process of “finding and eliminating” will consume all the system resources (CPU, RAM, etc.).
 – Tracking down Flash-DDOS attackers is very challenging: hackers only interact with third-party websites once to upload Flash content, and they have the freedom to choose! The attack process is self-occurring and asynchronous, so they only need to upload the content and then everything happens automatically. The victim’s system is almost unable to detect which third-party websites are “hosting” the deadly Flash (unless the hacker is incompetent and exposes the referrer in Flash requests—this case is becoming increasingly rare). Only the users being exploited for the attack or ISPs can directly access the third-party websites that are “hosting” the deadly Flash; users cannot and do not need to know, while ISPs may know and are not obligated to act! The victims suffer the most and feel the loneliest—especially if they are businesses operating online—e-commerce enterprises.
– Tracking down Flash-DDOS attackers is very challenging: hackers only interact with third-party websites once to upload Flash content, and they have the freedom to choose! The attack process is self-occurring and asynchronous, so they only need to upload the content and then everything happens automatically. The victim’s system is almost unable to detect which third-party websites are “hosting” the deadly Flash (unless the hacker is incompetent and exposes the referrer in Flash requests—this case is becoming increasingly rare). Only the users being exploited for the attack or ISPs can directly access the third-party websites that are “hosting” the deadly Flash; users cannot and do not need to know, while ISPs may know and are not obligated to act! The victims suffer the most and feel the loneliest—especially if they are businesses operating online—e-commerce enterprises.
The Beast and the Ego of the “Netizen”
Internet’s shortcomings will further expose human egos. Flash-DDOS is extremely dangerous, easy to execute, and almost impossible to defend against or track down the perpetrators!
The First Ego – The Desire for Power
Controlling someone else’s information system is a form of power! To gain this power, legitimate hackers must study and work very seriously for a long time (5-10 years). For them, the ultimate goal of hacking is to gain control over the entire system—it can be seen as a hobby, where they do not destroy or deprive others of their efforts. It is an intellectual game that promotes the development of information systems.
Many people want this power, but they do not want to work and do not want to wait long! They use the “DDOS beast,” wanting the simple power to make a system go down, and from that, they believe they have attained ultimate power—the power of life and death!
In reality, they have put an end to their path of becoming legitimate hackers and stepped into darkness with very shallow knowledge and goals. The interesting point of the game is in the process of playing; what matters about the outcome?
Why play a game where you have so many advantages, forcing others to participate while causing significant damage to society?
The Second Ego – Greed and Incompetence  Recently, there have been many DDOS attacks for economic reasons; newly formed e-commerce businesses, in the midst of competition, have “mobilized” DDOS as a means of competition and to gain first-mover advantage in this highly volatile market!
Recently, there have been many DDOS attacks for economic reasons; newly formed e-commerce businesses, in the midst of competition, have “mobilized” DDOS as a means of competition and to gain first-mover advantage in this highly volatile market!
The coin you spend to hire a DDOS is a shovel digging the grave for Vietnam’s e-commerce—your own as well. Think carefully and act wisely! Create good products, affordable prices, and attentive services; the market will have its own choices.
The Third Ego – Extreme Selfishness and Deceit
To solve the DDOS problem, it requires the cooperation of many parties: end-users, ISPs, lawmakers, experts, etc.
Recognizing the threat of DDOS, we are still slow in extending our arms to collectively tackle this issue. We are barricaded in our personal shells, waiting for a miracle to occur so that DDOS ceases to exist. This is impossible, at least for the next five years; it is time to take action!
As experts, we must be honest and truly have accurate assessments of this disaster. Deceit for any reason is unacceptable. We cannot have any traces or information from logs on systems; let’s speak the truth about the ability to investigate DDOS to the community and collectively understand the nature of the problem, from which we can propose coordinated solutions! Do not conceal information about an “epidemic”—something that every doctor understands!
Conclusion
DDOS and other forms of attacks on the Internet can be mitigated with strong determination and a robust dismissal of our egos, along with the enthusiastic and responsible collaboration of ISPs. The establishment of VNCERT is a response to the great expectations of Vietnam’s e-commerce community. I still have great faith in the stability of the Internet in Vietnam in the near future.
Kiet D.Anh (The Connections Magazine)




















































