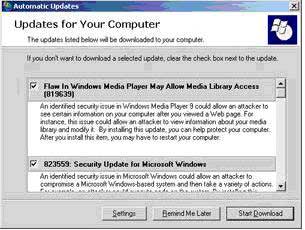
Perhaps all of us have experienced data loss incidents due to viruses, hackers, and system vulnerabilities. Therefore, since 1998, Microsoft has introduced a method to update patches when using the Windows operating system through the website www.windowsupdate.com. When using Windows XP or Windows 2000 SP3 and above, we gain a new feature called Automatic Updates, which can automatically connect to the Windows Update website to download system patch files.
The Automatic Updates program automatically updates patches
However, in a distributed environment, updating individual patches for the system often does not yield high efficiency due to various reasons such as bandwidth issues and management difficulties caused by user negligence. Therefore, in the role of IT Supervisor or Network Administrator, we certainly want a more effective processing method. Fortunately, Software Update Services (SUS) can solve this problem for us. With SUS, we can manage the updates of system patches for users through one or more SUS servers. The Automatic Updates program on users’ computers will be configured to connect to the SUS server to download updates instead of from Microsoft’s website. This will help us manage the system update process more effectively with mechanisms such as scheduling updates for clients or specifying the files to be installed based on the domain policies.
In this article, I will present the method of installing and configuring the SUS server and setting up domain policies in a practical model for a client company with over 50 users to manage and implement system updates more effectively.
The TestLab model requires the following machines:
Step 1: Install and Configure Software Update Services
Software Update Services (SUS) is a completely free product that can be downloaded from http://www.microsoft.com/downloads and installed on susserver.mcsesecurity.com. The installation process is relatively straightforward; we only need to specify the location to store the program’s necessary files and follow a few instructions as shown below.
After the installation process is complete, the next step is to log into the management website http://susserver.mcsesecurity.com to synchronize data with Microsoft’s update server and perform some necessary configuration operations.
The administration website of the Software Update Service server
Click on Synchronize to start downloading patches from Microsoft’s server. Due to the large volume of updates, the data synchronization process may take a considerable amount of time. To minimize bandwidth usage, we should schedule this process to occur outside of working hours by selecting Synchronizer Scheduler and setting the parameters as follows:
When the synchronization process is complete, depending on your system, you can select the necessary hotfixes for clients to update through the Automatic Updates utility by selecting Approve updates and checking the files needed for the machines on the network:
The list of patches and options
Thus, we have installed and configured the SUS server. Next, we just need to configure the automatic update program on client machines to connect to this server to download and install the patches. If the client machines on the network do not yet have the Automatic Updates utility, we can download it from Microsoft’s download site and distribute it to member machines through Group Policy or guide users to install it from a shared folder, checking in Control Panel after the installation process is complete to ensure that Automatic Updates is present on their systems.
Step 2: Configure Group Policy on the Domain Controller
We manage the process of updating patches for clients through Group Policy on the domain management machine with the following steps:
1. Select Start -> Programs -> Administrative Tools -> Active Directory Users and Computers
2. Right-click on the domain and select Properties, then choose Group Policy, select Default Domain Security Policy, and click Edit to open the policy editing frame of the domain, then select Add/Remove Templates as shown below:
3. Select the ADM (administrative template) named wuad.adm and click Open
4. Then we edit the policy by clicking on Automatic Update in the right pane of the WUAU-ADM template and select Auto download and schedule the install and specify the date and time for the clients to download the system update files as shown below:
5. Next, we click on Specific intranet Microsoft Update server location and select enable, then enter the name of the SUS server and click OK:
Thus, we have built the SUS server system and established the necessary policies for clients to download patches from a specific server in the domain system. The next step is to run the command hGPupdate.exe from the Run command and require users to restart their systems when possible.
Note: For computers in a Workgroup environment, we can still implement this model by changing the local policy of each machine
To ensure system safety in case of incidents, we should back up the necessary data of the SUS server. To back up SUS, we need to back up the contents of SUS, the SUS administration website, and the IIS metabase. You can find more information on this issue on Microsoft’s site or contact the email address at the end of this article for further details.
However, some patches may cause older applications on the system to operate unstably. Therefore, for critical systems, it is advisable to thoroughly test the patch files on test machines and carefully refer to the manufacturer’s information regarding their side effects. To identify which computers on the system have not timely updated these vulnerabilities, we should use automated scanning programs provided by Microsoft, such as Hfnetchk or MBSA. These are programs that can be downloaded for free from the Microsoft download website.
References – You can download books, demo video files, and programs at the following addresses:
http://www.security365.org/downloads/books
http://www.security365.org/downloads/demo
http://www.security365.org/downloads/software/
Nguyễn Trần Duy Vinh, NetManager – MCP
Safety Solutions Company
www.security365.org